INDUSTRY 4.0
SOFTWARE THAT ALLOWS YOU TO MANAGE DIFFERENT SYSTEMS IN FACTORIES EASILY
What Is Industry 4.0?
Industry 4.0 is a set of three-phase systems: the internet of things, big data, and cyber-physical systems. It’s a project to bring the information world and the industry together. In parallel, this structure plays an important role in the formation of smart factories. It is based on the principle that the systems are connected to one another.
iSIM Industry 4.0 Platform stands out with its innovative architecture that can create the necessary infrastructures for communication, correlated data, automatic decision making, trend analysis and prediction of all subsystems. Designed with the modern architecture of today’s technology, iSIM offers a flexible and scalable infrastructure, with years of hands-on experience and user demands.
iSIM Industry 4.0 Platform also allows companies to manage their operations at lower costs which makes it unique in efficiency.
Factories require various types of sensors, softwares and solutions from different suppliers and brands. However, integrating them on a single platform is a challenge which can negatively affect the rapid and accurate decision making mechanism.
At this point, iSIM Industry 4.0 Platform comes into play to face this challenge. iSIM collects all the data from sensors, softwares and other endpoints and displays it on a single screen after converting it to meaningful information. This fast analysis helps our clients get an overall view of tasks and make quick and accurate decisions.
Benefits of iSIMPlatform Industry 4.0 Technology
iSIM Industry 4.0 Platform predicts and prevents potential damage before failure occurs in generators, factories, treatment facilities, elevators, tunnels. It extends the life and efficiency of equipment, enables corrective maintenance for critical elements, and reduces downtime in processes and devices, reduces labour costs up to 12%, increases profitability and energy savings while reducing employee workload.
The distinguishing features of iSIM Industry 4.0 Platform are the on-Premise and Cloud installation facility, 100% Web-based Architecture, adaptive and simultaneous updatable workflow, powerful instrument panel that can be adapted to the needs, and the Microservice Architecture which uses the Kubernetes and Docker Container infrastructure.
iSIMPlatform Advantages
According to studies, the following advantages have been discovered in the businesses of companies that have used predictive maintenance.
Increase in OEE
Reduction in deteriorations
Increase in production capacity
Increase on ROI
Main Concepts of Industry 4.0
Big Data
Augmented Reality
Cloud technology
Cyber Security
Internet of Things
system Integration
Gains by iSIMPlatform
MALfunctıon reductıon
paperless busıness
enchacement ın ınterventıon tımes
reductıon ın setup tımes
WAITING TIME RECUTION
Oee / productıvıty growth
digitalization of manufacturing
Our response to the shared requirements will be by providing a holistic solution that will resolve current highlighted issues and that will be the foundation of future Industry 4.0 elements for factories.
Collectıng data from the field
Data Analysis & Correlation
Digital Consulting
Alarms & Reporting
User Friendly Interface
Integration with 3 rd party systems
iSIM In Industry 4.0

Functions
Integration into Different Systems
One-Stop Management
Adaptive Workflow (SoP)
User Friendly Interface
Communication with Other Command Centers
Dynamic Screen Management
Detailed Analysis and Reporting

Benefits
Real-Time Monitoring and Management
Collecting, analyzing and making sense of data
Analysis, Instant Status Notification and Reporting
Quick and efficient response to an emergency or alarm
Elimination of chaotic structure
Cost Optimization
Reducing the errors caused by the human factor
iSIM Industry 4.0 Management Screens
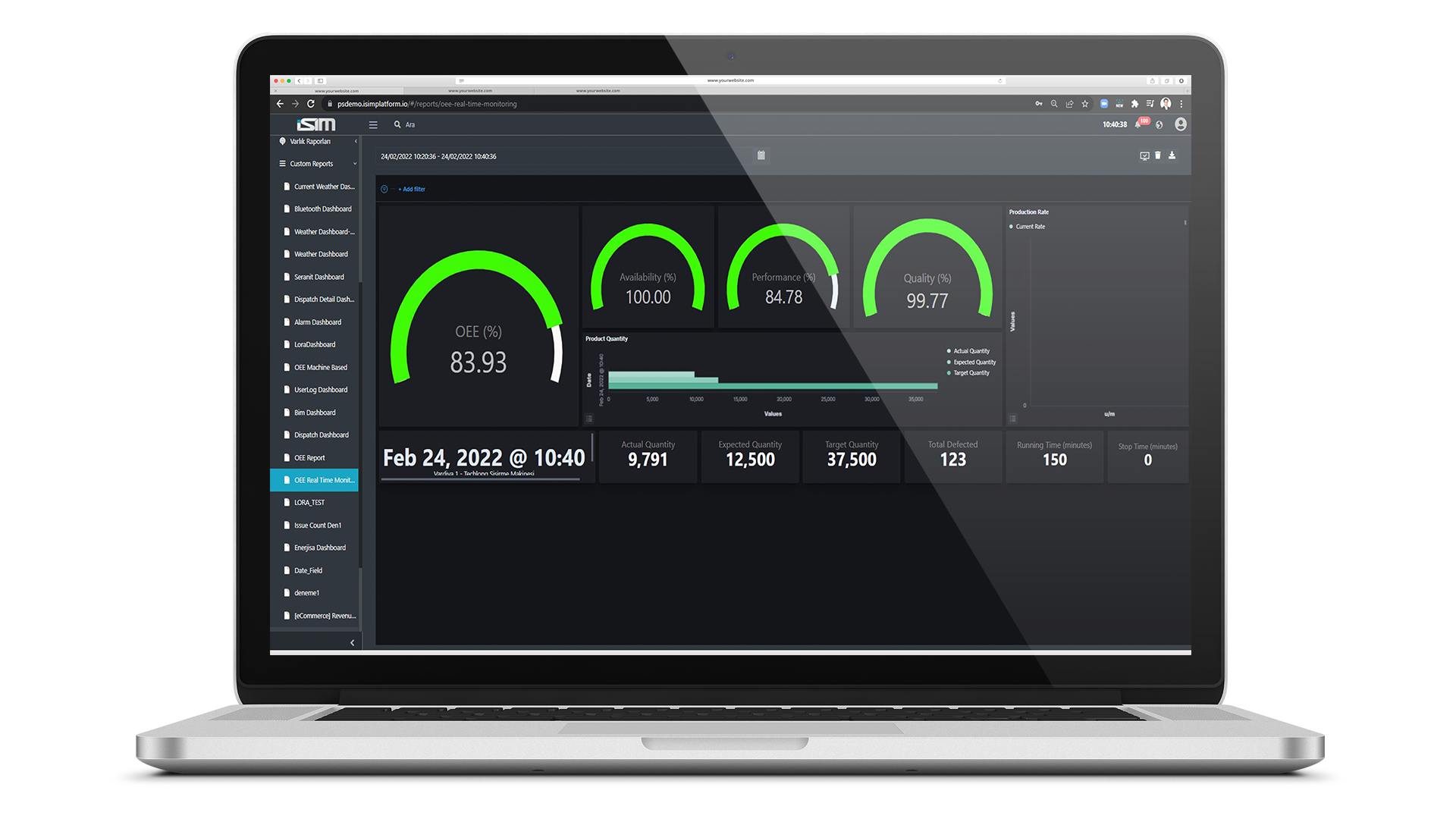
OEE Reports
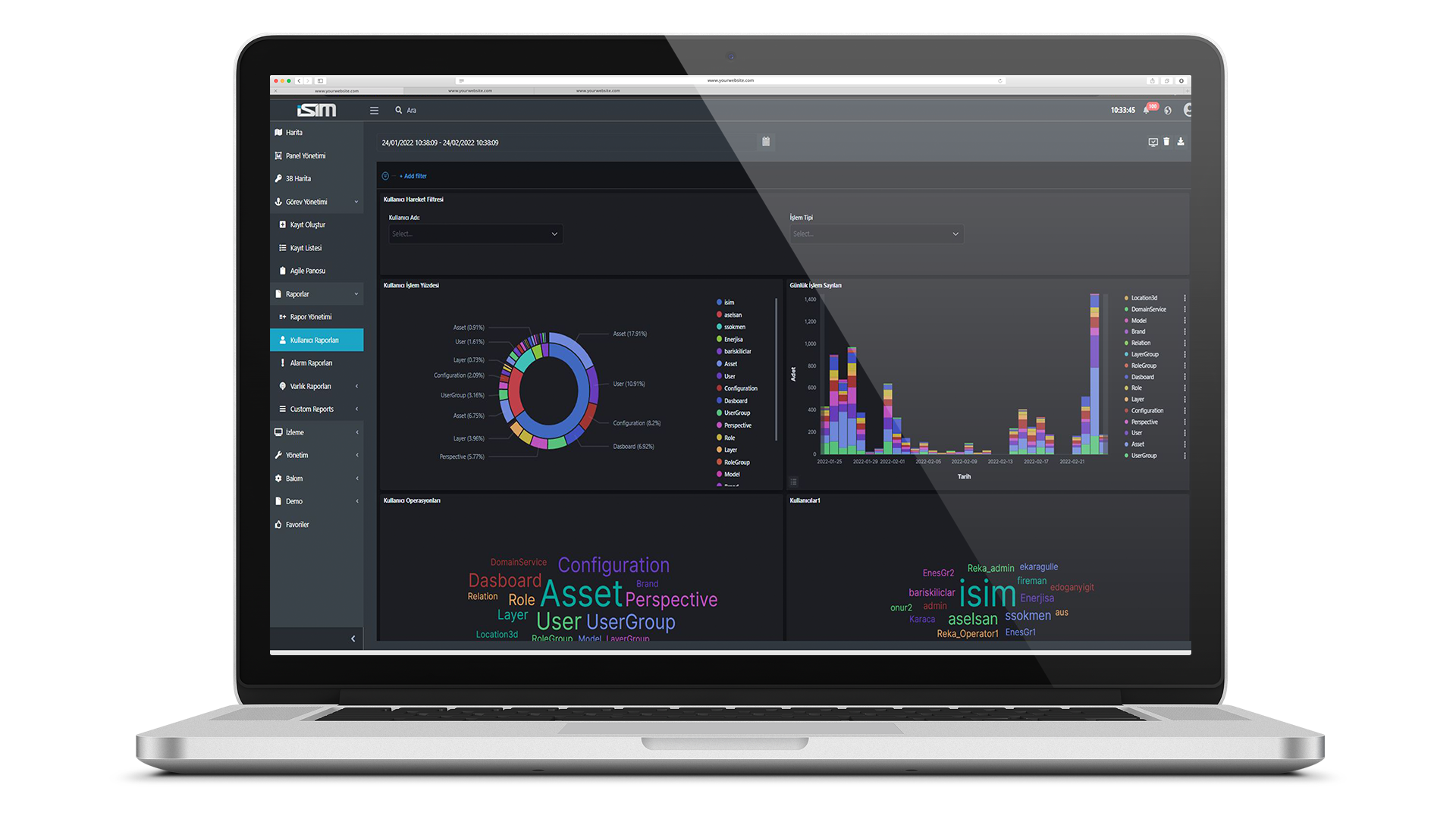
Production Reports
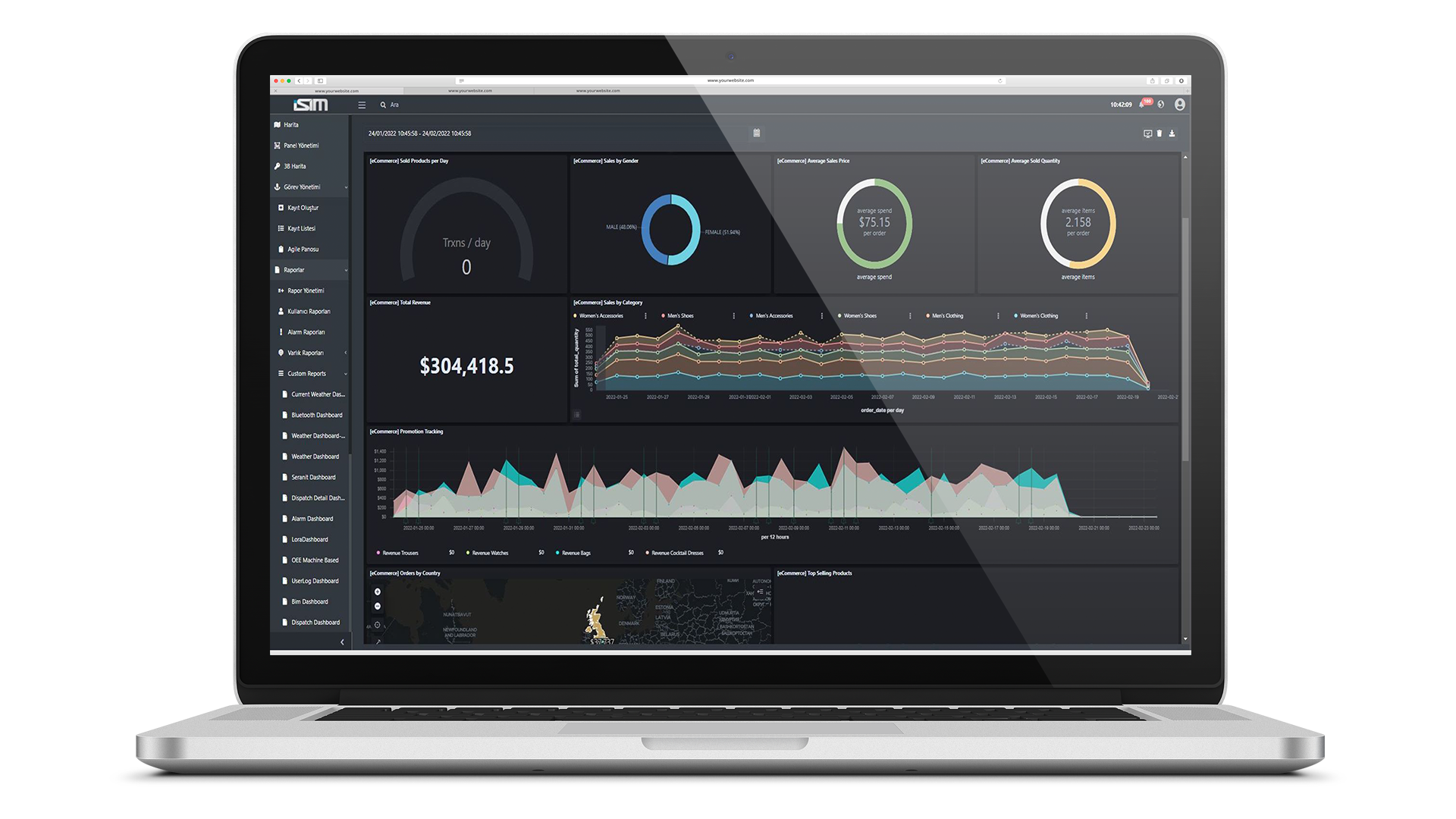
Adaptive Reports
Production Line Management System Using IoT Sensors
Data collected from sensors can be shared with relevant people via e-mails, notifications, mobile platforms, and websites.The production line management system based on IoT sensors will assist decision makers by providing accurate information from the sensors. Efficiency will be able to increase as a result of having accurate information.
Sensor Management and Monitoring
Production Forecasting and Analysis
Real Time Notification Via Email, Notifications, Mobile Platforms and Websites
Real-Time Monitoring and Management with Graphical Dashboard
Capabilities Of iSIM

Task and Procedure Management
Remote Monitoring And Measurement
Sensor and Endpoint Monitoring
oEE Reports
Event and Alarm Management
Scada Integration And Monitoring
eRP mRP İntegration
Advanced Reporting and Trend Analysis
Unusual Situation Detection
Industrial Equipment Monitoring
2D – 3D Floor Based Plan Monitoring
Predictive Maintenance
Asset Tracking
Building – Facility Management
Energy Monitoring
Security Systems Management
Alarm management and adaptive workflow
With Adaptive Workflows, any type of alarm can be managed from birth to death.
The system is flexible to create and follow different scenarios and processes for various kinds of alarms.
The Workflow for Alarm and Incident Management is a unique feature provided by iSIM; multiple alarms and incidents can be managed at the same time.
Through the Dynamic Workflow Structure, iSIM Platform gives users the freedom to create their own alarm and incident management panels.
Which Protocols Are Supported By iSIM?
Network
TCP/UDP, REST, HTTP, WebSocket, WebRTC, SOAP 2.0, NTCIP, RTSP, ONVIF
Message Queues
MQTT, Apache Kafka, RabbitMQ, ZeroMQ
Big Data
ElasticSearch, Hadoop, Apache Spark
Social Media & Messages
E-Mail, Twitter, Slack, Telegram, Physical Documents
Static File Database
Microsoft SQL Server, Postgre SQL, MongoDB, CouchDB, ArangoDB Neo4j, Low-level I/O, GPIO
Cloud Services
Microsoft Azure, Amazon AWS, Google Cloud Platform
SCADA & PLC
OPC UA/DA, BACnet, KNX, Modbus TCP/RTU/ASCII, Profinet Profibus, PPI/PPM, ADS, FINS, Host Link, C-mode, DF1, FACON TCP, FACON Serial, Fanuc CCM, Fanuc SNP, Fanuc SNPX, CI Protocol, DirectNet, Melsec, Sucoma, Lecom
Security Standarts Of iSIM
128 Bit SSL Encryption
HTTPS Communication
Bidirectional Encryption
Password Protected
Digital Signature
Certificate Based Encryption
Role Based Protection
Windows Active Directory
Two-Step Authentication
Our other solutions
transportation
As a result of iSIM, more effective intelligent transportation systems will be readily available such as the Red Light Violation Detection System, the Variable Message System, the Corridor Speed Enforcement System, and the Parking Violation Detection System.
Physical Security
It is possible to manage small or large areas using iSIM Physical Security tools, which include security cameras, access control systems, radars, buried cable systems, and smart fences. IGA preferred iSIMPlarform for security management.
Smart cities
iSIM is used to manage sensors for a variety of applications, including lighting, waste management, weather control, energy management, and smart agriculture.
